Challenge: Speed of time isolating cyber threats
Solution: Keysight Threat Intelligence plus correlation and reporting in CySight
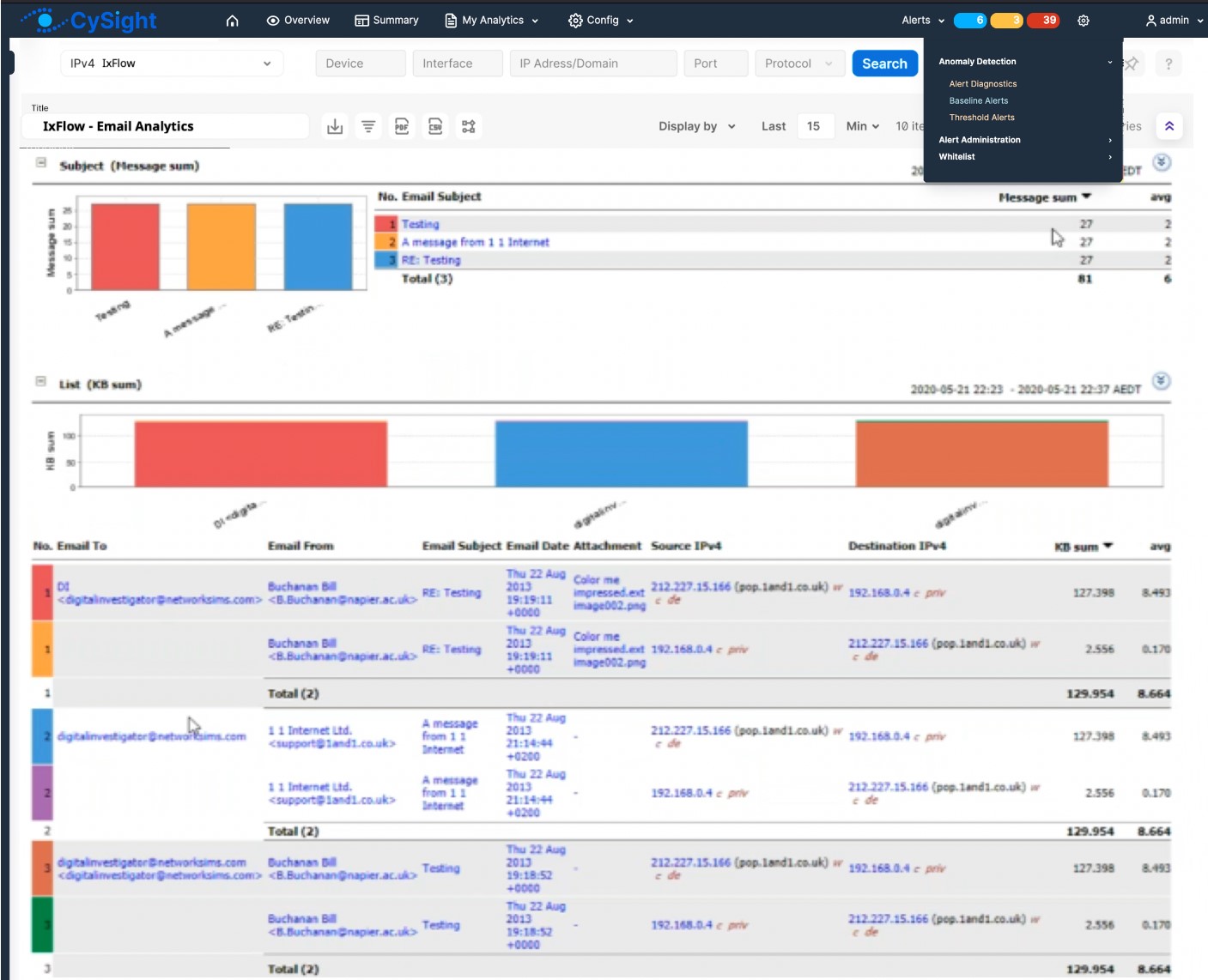
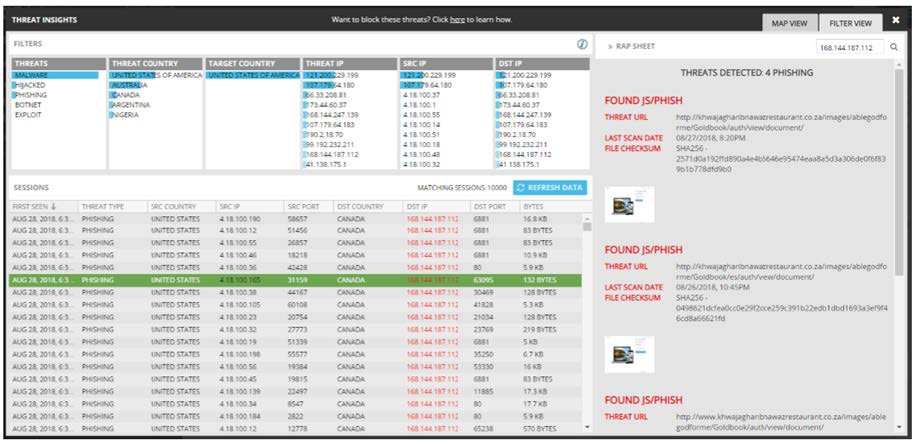
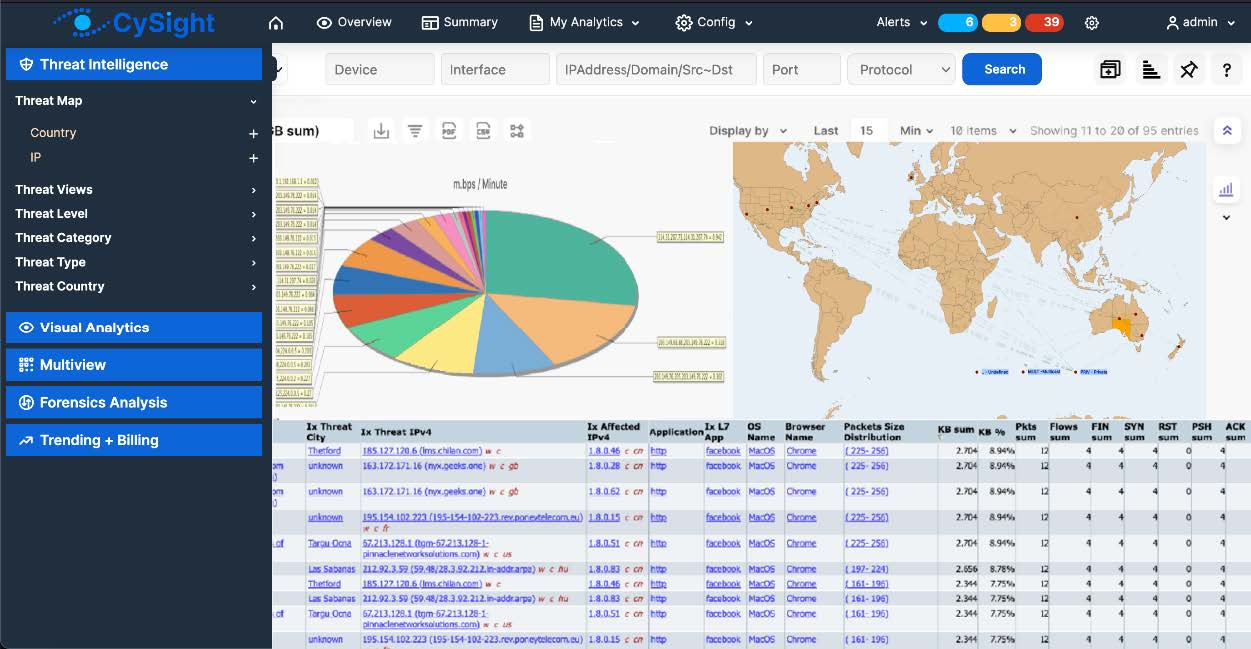
Response: Keysight Threat Intelligence data exposes details of botnet, malware, hijacks, exploits – which is exported to CySight in IxFlow records. When correlated by CySight with additional IxFlow fields and other metadata, cyber threats can be quickly isolated/mitigated e.g.;
- For malware find out not only affected IP address, but which user login and geolocation as well – to quickly triage the issue.
- For an exploit identify particular OS, Devices, and Browsers impacted, so that patching can quickly be updated.