Even with advanced firewall technology, intrusion prevention systems (IPS), and a wide array of security tools in place, businesses still miss clues and suffer major breaches every day. Why? Because of the sheer volume of alerts being generated places a huge processing drain on the security team, as well as the infrastructure itself. This translates into wasted time and money, and increased risk of falling victim to attack. Outbound exploits are also growing much more dangerous and harder to detect.
Two Types of Traffic Hit Your Network
Much of the traffic on your network simply doesn’t belong there. This includes traffic from sites that:
- Distribute malware.
- Are used to conduct phishing attacks.
- Serve as botnet command and control (C&C) centers
- Have been hijacked for nefarious purposes.
Using a Threat Intelligence Gateway like ThreatARMOR can mitigate the cost and complexity of securing your network. By pre-filtering known bad IP addresses and traffic from untrusted countries you can stop unwanted traffic from ever reaching the firewall.
Why can’t we simply configure our existing next-generation firewall (NGFW), to block these malicious IP addresses?
You can, but most of these devices have limitations.

First; rules in an NGFW cost CPU and memory resources, and most run out of capacity at about 10,000 rules. A threat intelligence gateway can handle millions of rules pertaining to IP addresses. A product like ThreatARMOR automatically downloads updates from the ATI Research Center as frequently as every five minutes, giving you the most up-to-date list of known bad actors. If it’s known bad, why pass it to the NGFW’s to process?
Second; you want your NGFW to analyze application-layer events, which is the purpose of its design, not to understand the global Internet. Simply put, using ThreatARMOR to filter network traffic based on Ixia’s continually-updated security intelligence will make your NGFW perform better.
21,000 hours per year are spent dealing with false positive security alerts
Ponemon Institute, 2015
ThreatARMOR eliminates 30% of bad false positives saving 6,300 hours per enterprise
Average IT Security Operations Salary = $100K
Payscale (US Based Median), 2015
}
157
WEEKS SAVED PER ENTERPRISE
$300K+
OPEX SAVINGS
ROI: 15x
BLOCK the unwanted from entering or exiting your network
GET MORE out of your security team and tools
LEVERAGE Ixia's professional-grade Application and Threat Intelligence feeds
SAVE YOUR SECURITY TEAM FROM WASTING CYCLES
Out of Band or Inline
You can install a Threat Intelligence Gateway inline or out of band.
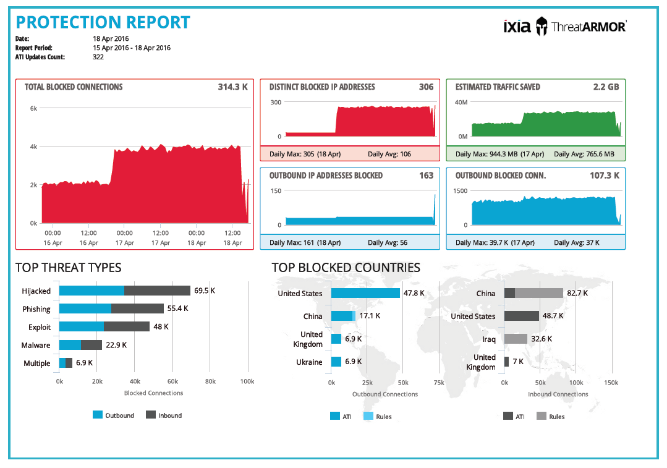
A phase one implementation can be out of band and informational. Of course it cannot block malicious traffic in either direction however it can provide the Protection Report:
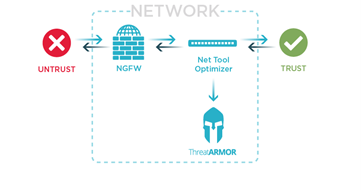

Phase 2 implementation with ThreatArmour can be inline in full protection mode.