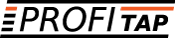
In today's modern network architecture, monitoring and security tools are required to handle traffic coming from multiple visibility devices including network TAPs or SPAN port. Each of these tools are required to see a different set of the network traffic without overwhelming these tools. Network Packet Brokers (NPBs) are able to address this challenge by providing a more centralized and intelligent way to manage data forwarding to the monitoring tools.
To do all this, however, NPBs must be capable of managing the relentless growth in network traffic, the multiplication and constant evolution of monitoring and security appliances also the increasing complexity brought by virtualization technologies.
Next-Generation Network Packet Brokers (NGNPBs)
To accommodate this need, NPBs capabilities have evolved. Aside from its core functionality such as intelligent aggregation, advanced filtering and load balancing, the NGNPBs offer the following extensive set of features:
- Packet
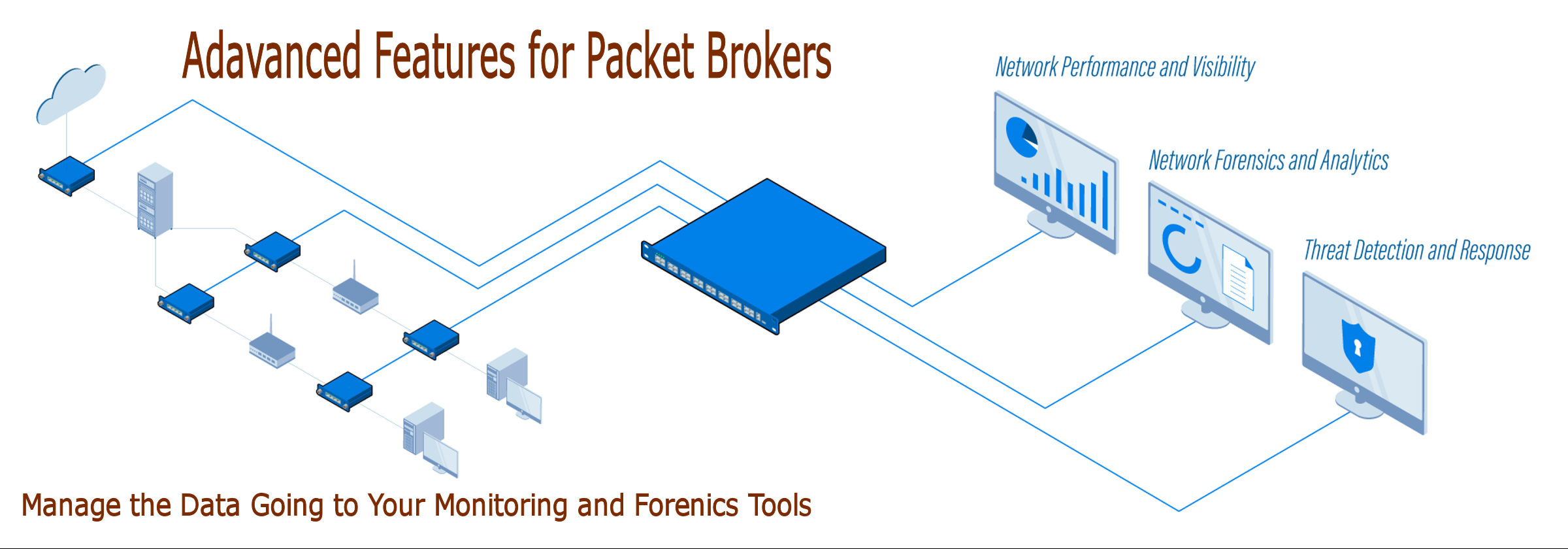
De-Duplication - Packet
Slicing - Time
Stamping - GRE
Tunneling - TLS/SSL
Decryption & Encryption - Load
Balancing - GTP
IP Filtering
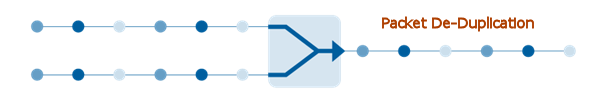
When you are trying to troubleshoot and identify points of delay in application performance more capture points are always better. With multiple capture points such as span ports or the use to TAPS can lead to duplicate packets being sent to your security and monitoring tools
A SPAN port can generate multiple copies of the same packet and transfer that data to your security and monitoring tools. These copies are exact duplicates of the original packet. Even when optimally configured, a SPAN port may generate between one and four copies of a packet and the duplicate packets can represent as much as 50% of the network traffic being sent to a monitoring tool.
It also matters where you capture monitoring data, as this can create duplicate data as well. If you capture the data at the ingress to the network and then again in the core, you have probably copied the same data twice. This double capture is in addition to whatever duplicates were made by the core switches themselves. This along with redundant network architecture leads to duplicate packets being sent to your monitoring tools resulting in inefficiency.
Challenges with Duplicate Packets
So the elimination of unnecessary packets from the data inspection process will improve the capacity of data that your monitoring tools can process. A 50% reduction in the amount of data that needs to be processed is a significant reduction. This can result in a sizable cost savings for your network, as you should be able to decrease the number of unnecessary tools that you need.
- Duplicate Packets can skew network trending analysis
- Over-subscribed bandwidth on the ingress port of the monitoring tool
- Increased resources to inspect packets
- Some packets not inspected
- False positive errors – some tools report errors when duplicate arrive
- Compromised data analytics
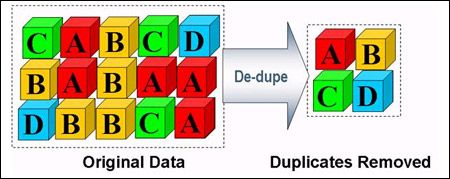 Network Packet Brokers can eliminate duplicate packets before being forwarded to your monitoring tools. With packet deduplication, similar copies will be dropped from the data stream to reduce overhead. When your network monitoring tools don't have to deal with problems associated with duplicate packets, they can store and process as much useful data without the unwanted duplicates being transmitted to them. This will increase the visibility across your network and allow your tools to accurately perform its tasks.
Network Packet Brokers can eliminate duplicate packets before being forwarded to your monitoring tools. With packet deduplication, similar copies will be dropped from the data stream to reduce overhead. When your network monitoring tools don't have to deal with problems associated with duplicate packets, they can store and process as much useful data without the unwanted duplicates being transmitted to them. This will increase the visibility across your network and allow your tools to accurately perform its tasks.
Increase Tools Bandwidth
By removing redundant data, most data centers can double or triple tool bandwidth
- Increase recordable time on the network tool providing greater visibility
- Increase monitoring tool performance
- Generate more accurate tool statistics more precise session analysis
- Inspect packets for duplication, recognizing acceptable differences in MACs / VLANs
Traditionally done at the analyzer, packet slicing allows you to truncate the packet at different offsets for each packet or the type of packet to be sliced. This can be useful when the analysis you require is centered on nodes, protocols and flows but not the payload information
Networks Analyzers only have a limited amount of data storage. If the analyzer can't cope with the amount of traffic, then packets are more likely to get lost. To prevent this from happening, you need to make sure your analyzer isn't being wasted on maintaining unnecessary packet payload. By removing payload that is irrelevant to your network monitoring and security analysis. When the payload is reduced, the system can run more efficiently.
When using packet slicing, the packet broker slices a packet to the size of the frame through the header. If you remove payload data from packets and leave only the header information, you ensure that only the right data is captured and sent across to the appropriate tool. As a result, the performance of your tools will be improved as the throughput and storage space are reduced. another benefit of this feature is in security compliance. With packet slicing, you will be able to take out confidential data before it reaches your monitoring tools. This to ensure that this sensitive data is not being stored outside secure boundaries.
Benefits of using a Packet Broker for Packet Slicing
- Reduces bandwidth going to your monitoring or security tools
- Allows you to perform this function at the packet capture level anywhere in the network.
- Can specify the type of traffic that is being sliced.
- Reduces the amount of data that is collected and analyzed by the security or network monitoring tools.
- Reduces the storage required by the security or network analysis tool
- Greater Security – by removing confidential data like passwords, financial accounts, or media data at the point of capture, reduces your chance for a privacy breach.
- Regulation Compliance – Hidden confidential information allows you to remain complaint with regulations mandating privacy best practices such as SOX, HIPAA and PCI DSS.
Types of Packet Slicing
- Fixed slicing: Truncation of frames to a maximum size
- Dynamic slicing: Truncation of frames to a dynamic size relative to a specified protocol, (e.g IP Payload + 16 bytes).
- Conditional slicing: Fixed and dynamic slicing with properties based on frame decoding.

Why Time Stamping
To measure network performance we gather network data from many network links using SPAN or network TAPS and aggregate this data to a single analysis port on our network performance and security tools.
We use the timestamp on the packet to correlate different events when troubleshooting network and security events, but the aggregation process can add a delay to the packet making the timestamp inaccurate.
Time Stamping on your packet broker
Using timestamps on your packet broker means that you can side-step any delays introduced by the aggregation process. Time Stamping will record the precise time that the first bit of packet arrives at the input port which ensures that downstream monitoring and security systems can accurately reconstruct the original timing of data even if aggregation delays are large or variable. And since delays no longer matter, large buffers can be used without penalty to avoid packet drops. In practice.
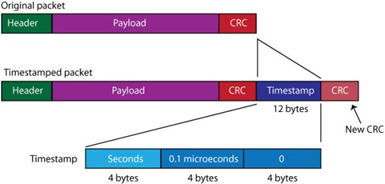 A 12-byte timestamp – and new CRC added to each packet
A 12-byte timestamp – and new CRC added to each packet- Records the precise time that the first bit of the packet arrives at the input port
- Use of GPS NTP Time source can prevent drift of counter
Packet Brokers can encapsulate and de-encapsulate data to send and receive it from different sites and platforms within your environment. Encapsulation is mandatory for security reasons while packets traverse a WAN.
Beyond scalable aggregation, replication, packet brokers can provide access to traffic through a variety of complex tunneling protocols such as, Encapsulated Remote SPAN (ERSPAN), Generic Routing Encapsulation (GRE), Virtual Extensible LAN (VXLAN). These advanced tunneling features will help you to ease blind spot of multiple traffic traversing on network anywhere within your IT infrastructure whether it is locally or remotely, physically or virtually.
Track packets easily by adding IDs to packets based on the source (ingress) port and remove them as they leave the packet broker via exit (egress) ports. Using this approach, packets are encapsulated and directed from a switch/VLAN to a target IP endpoint with GRE or ERSPAN tunneling and send to the appropriate tools. Also, by identifying and stripping the protocol, Network Engineers can selectively dictate which types of traffic should be routed to a specific device for further analysis.
 Remove a Potential Threat Vector and Secure your network with complete visibility into all your encrypted traffic
Remove a Potential Threat Vector and Secure your network with complete visibility into all your encrypted traffic
Today over 90% of internet traffic around the globe is encrypted to protect your network and the end users. This protects sensitive information and identity theft, security breaches and data leaks such as credit card numbers, social security numbers etc
In 2018 over 2.8 million cyber-attacks were hidden in encrypted traffic
As most traffic becomes encrypted including with the latest TLS 1.3 cryptographic protocol cybercriminals can like a trojan horse use this to conceal malware, hide command-and-control traffic and cloak the exfiltration of stolen data.
You can use a packet broker to efficiently decrypt SSL traffic, and inspect the traffic for threats and malware share it with tools and then re-encrypt it exposing this threat vector

Two big challenges in monitoring 10 and 40 Gig networks is the security gap it creates and the overall performance of the monitoring tools. Existing security tools cannot keep up with the over throughput and bandwidth of the network.
Security attacks are also getting more sophisticated, and as a result the rules in the security devices are getting more complex. This means a lot of resources are being allocated to content inspection.
Adding load balancing at the Packet Broker level is a cost effective way to share the increasing traffic load among multiple inline tools. By load balancing you can deploy two or more appliances in parallel with traffic balanced between them.
Advantages of Load Balancing
- Tool sharing technology allows you to even traffic distribution maintaining session delivery across multiple tools
- Build efficiency of inline appliances by sharing a pool of them across multiple independent network links.
- Heartbeat and link fault detect ensure that all monitoring devices deployed have high availability and advanced redundancy.
- Relieve overloaded monitoring tools by distributing traffic, by flow, to multiple replicated tools working in parallel.
- Prevents oversubscription/packet loss (eg. monitoring 10 GigE traffic with Gigabit tools)
Inline Applications
Using Load Balancing with bypass switching technology we take full-duplex traffic and route it through the bypass bridge before distributing the traffic across multiple inline tools.
Out of Band Application
Traffic from the network flows into the Load Balancer and is aggregated and then load balanced to a number of data recorders and forensic traffic recorders. So when you need to capture specific or confidential information you are able direct traffic in one direction which does not go back to the network being taped.
According to Statista, mobile accounts for approximately half of web traffic worldwide and is projected to grow substantially in total traffic volumes. Most traffic generated will be real-time video and multimedia files requiring increased bandwidth and fast connections. As this demand will continue to explode, mobile wireless networks must expand greatly in capacities.
GTP is a group of IP-based communications protocols used to carry GPRS traffic within GSM and UTMS networks. It is designed as a carrier to transport actual mobile packets over the network via tunneling. The tunnel is a channel between multiple GPRS support nodes through which the hosts exchange data. All IP addresses in the GTP packets are for mobile network elements such as the base station and the serving gateway.
When IP tunneling is used to deliver IP traffic across the core network using GTP, there can be multiple layers of encapsulation and addressing within the IP traffic. That's where GTP IP filtering feature comes handy. This feature on your packet broker will allow you to filter by IP in GTP sessions based on information in the data stream to control data flows within your infrastructure. This can be done by configuring the device to pass or drop the encapsulated traffic that doesn't match the packet policy from mobile station through identifying the source and the destination.